
The US continues to be the top country hosting domains that serves web-based threats and the main source for exploit kit distribution at a global level, according to new research.
Statistics from Palo Alto Networks' Unit 42 show that the top countries hosting the malicious URLs and distributing exploit kits are Russia, China, Netherland, Australia, USA.
The study reveals that the number of malicious domains hosted in the US in the second quarter of the year dropped to 248, from 257 recorded in Q1.
Except for the Netherlands, where the number of malicious domains more than doubled in Q2, all top five countries saw a decrease in the number of malicious domains they hosted.
The most significant drop happened in China, where the number shrunk to just two, from 106 in the previous quarter. Russia also noticed a decrease to two malicious domains, from a previous 20.
Exploit Kits on the menu
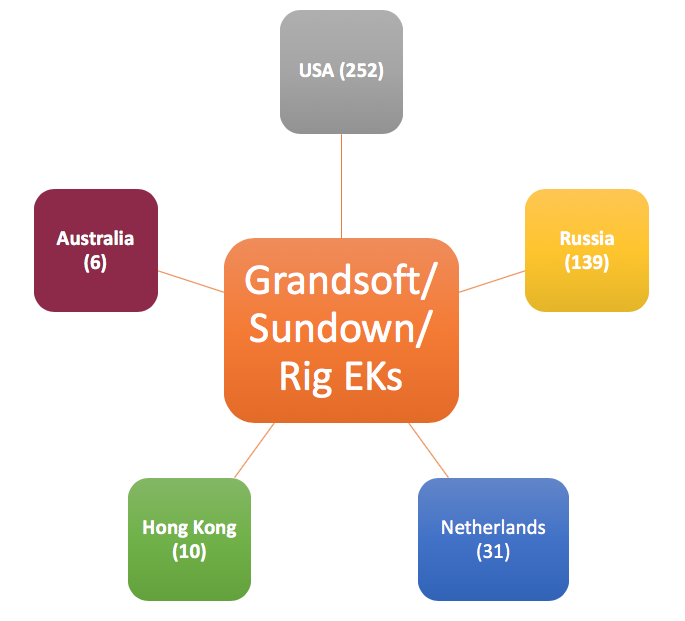
Only four exploit kits (EK) were active in the second quarter of the year: KaiXin, Grandsoft, Sundown, and RIG.
The US is also at the top of the list for EK distribution, Grandsoft, Sundown, and Rig being the main ones, and KaiXin coming in second place.
KaiXin, which attacks a 4-year old vulnerability (CVE-2014-6332), is more popular in Asia, where it seems to dominate, particularly in China and Hong Kong.
In Russia, exploit kit distribution is limited to Grandsoft, Sundown, and RIG exclusively.
Very old vulnerabilities still work
Cybercriminals are not particularly picky about the vulnerabilities they leverage, as long as they get to infect a good amount of computers.
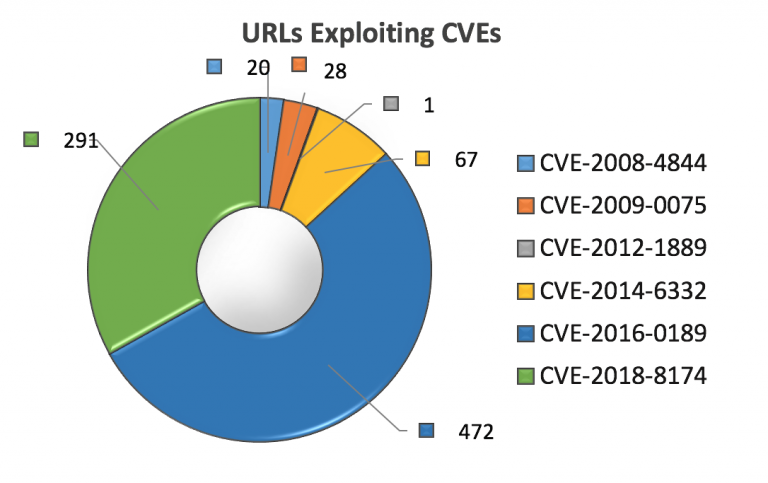
The research from Unit 42 reveals that EKs still rely on security bugs discovered more than nine years ago. For instance, exploits for CVE-2008-4844 and CVE-2009-0075, which affect Internet Explorer 5, 6 and 7, continue to be available from about 50 malicious URLs.
Other examples include vulnerabilities for OLE automation (CVE-2014-6332), one for code execution in Adobe Reader (CVE-2015-5122), and a scripting language flaw that affects Microsoft VBscript (CVE-2016-0189), which is the most used this quarter.
The newest security risk leveraged in exploit kits is CVE-2018-8174, a code execution bug in VBscript known as DoubleKill, which was used by Darkhotel APT in zero-day attacks.
Microsoft patched it in May, but once proof-of-concept code became available, it was quickly incorporated into RIG EK.
"In the realm of vulnerabilities, we see remarkable consistency, with a nearly identical roster of vulnerabilities under attack in this quarter as last quarter. The only notable addition to this roster is a vulnerability known to be used in zero-day attacks," Unit 42 report concludes.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now