It’s possible to make sense of webid AND do so without resorting to programming. Let’s see how, using only point and click. We know we have succeeded when we have made a post to a blogger site, used the semantic web as intended, viewed a certificate key, found its url , made a certificate (with said uri), and used the certificate to logon to https://idweb.cloudapp.net/.
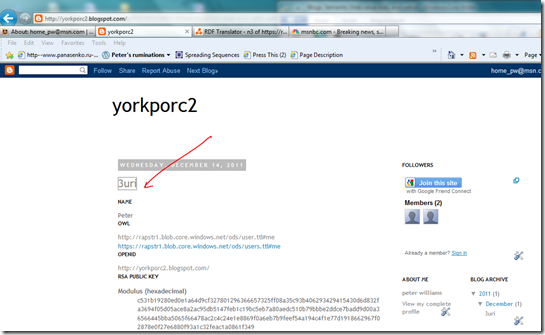
First, just browse to http://yorkporc2.blogspot.com/ and click on my profile page : http://yorkporc2.blogspot.com/2011/12/3uri.html. It’s always shown embedded on the home page, but we need to get there directly (so the semantic web works).
Let’s now invoke a viewer onto the semantic web, about the 3uri resource. To do so we invoke a bookmarklet (which can be added to one’s bookmark menu, as if adding a button to your browser). See http://uriburner.com/ and copy over the bookmarklet, yourself.
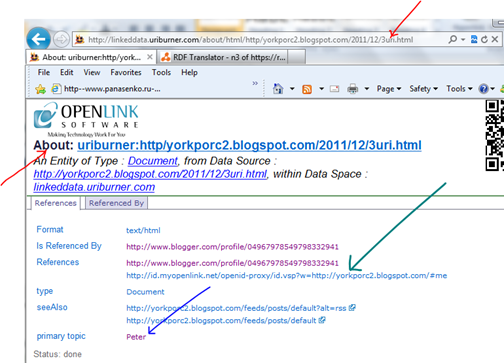
Because we were looking at 3uri itself (not the content of 3uri as happenstance embedded in the home page), we get:
This is the semantic web (as displayed in HTML for humans to see what the machines are saying about our documents). Yes, the semantic web does actually exist. You do not NEED to get out your programing tools. Just do the above.
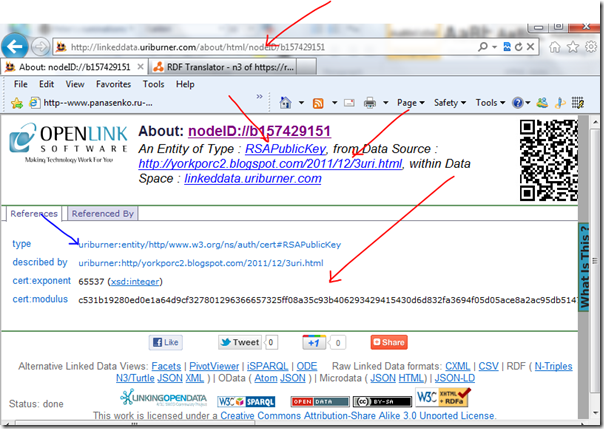
Given that to which red arrows point, we see that we are indeed describing our 3uri resource. The blue arrows point to the topic of that page (a clickable anchor, by the way). And the document even referenced that to which the green arrow points : an openid provider. It is one that is specifically tied to the information on our page, and invokes the finest spell that openid’s particular magic has to offer. But, more on that later.
This is cool. But, it doesn’t show much about the content on the 3uri page (information about certificate keys). But then, it is not supposed to; for that role is subsumed by the topic. Think like an android librarian moving robotically through the library space (and the semantic web gets easier). Or don’t, and just click the “peter” – since that’s the topic.
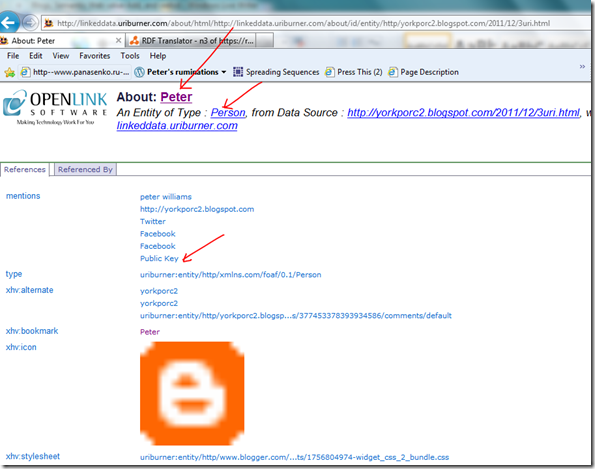
The first half of the page at least now talks about the content on my blog posting (vs. the librarian’s card catalogue, about sources):
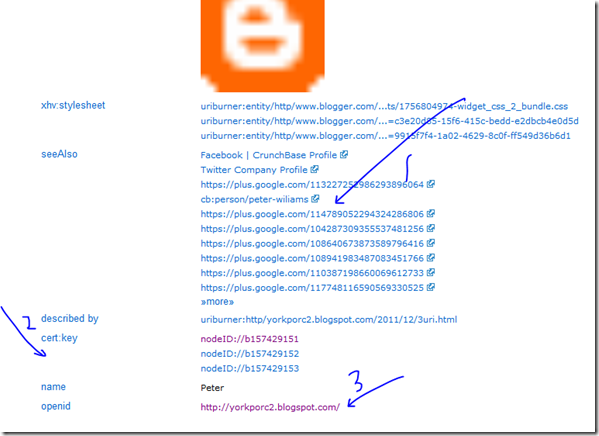
The second half is even more interesting:
It talks about seeAlso information – about OTHER ‘peter williams’. I am not too sure who sourced these relationships; with it possibly being Google who did it as a fringe benefit because Blogger is a Google asset. Not too interesting! But the cert:key is. Also interesting is the openid on show, a simpler variety of the openid we discussed earlier. But more on that later – once we use our openid WITH webid then to authenticate ourselves to some web site.
So what is this cert:key? Why are there 3 of them? And, what is the nodeID stuff? Is it a new brand of identity framework, competing with BrowserID?
So, I don’t know why there are three. But we can analyze what we have in one of them (particularly since all three present the same information, essentially).
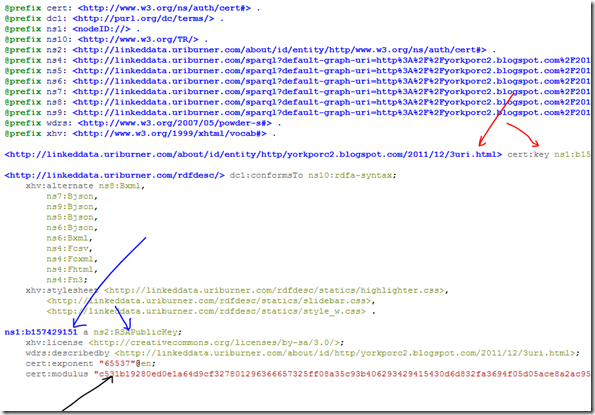
In the material pointed to by the red arrows, we see that indeed we are looking now at the content that I typed on my blog post. Great! And, we learn that all along I was describing my public key (great) which is recognized by the machine having denoted it as being an entity of type ‘RSAPublicKey’. Well done semantic web!
That page can itself be viewed technically – since the version we are seeing and with which we are interacting is formatted for humans to use, by point and click.
And do you just notice what happened? The semantic web just described the semantic web and even told the world how to repeat that feat. But let’s save that fun for another day.
For our purposes, the material identified by the red arrows shows the semantic web itself describing not merely my page but “the web” as a “generator” of a “derived” page in its own right – one that others can consume in a manner distinct from the page that it is describing (my blog post). This is like one taking a photo of a photo of you, and referencing the outer photo. It’s got a new title, but the content is the same (my still recognizable, ‘photographed’ public key).
So, someone (the semantic web itself) has made a document (on the fly) using my cert key, and bound it to my “about name”. Who is the ‘abouting’ party? It happens to be denoted by the first red arrow: <http://linkeddata.uriburner.com/about/id/entity/http/yorkporc2.blogspot.com/2011/12/3uri.html>.
Mr. Machine <http://linkeddata.uriburner.com/> tells the world that it talks “about” what it considers to be an “identity” (id) of the “entity” described at 3uri.
I call this my “about” name, and there can be N of them – issued by whomsoever wishes to talk about me (or 3uri, more specifically). It’s a URI, it is clickable, and thus I can give this string to folks and they can see the above. They can even repeat the semantic web re-rendering of — vs. “talking about” — my about-name (versus my “original” name of a blog post). Phew! Fortunately, we already viewed it, earlier!
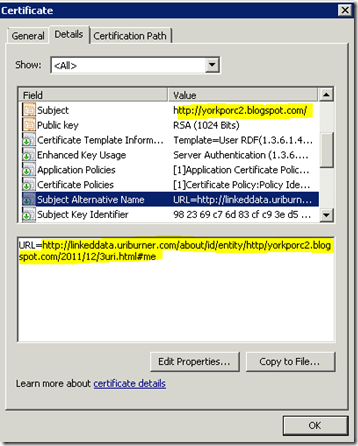
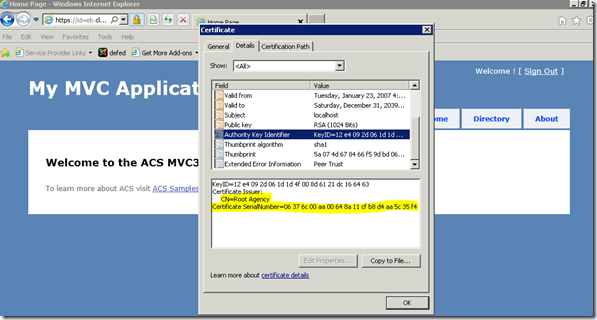
So, let’s now take that URI and put it in a certificate:
Here we see me (again back in charge, taking power away from the machines) saying that my subject name is http://yorkporc2.blogspot.com/ and there is an alternative name for it (that I hereby deem as an “authoritative” about-name, of the N folks’s about-names that anyone MIGHT give me (whether I like it, or not). But, of course I might deem multiple of them to be authoritative, should I wish.
So now I have a certificate, let’s use it! And here is where it gets REALLY cool.
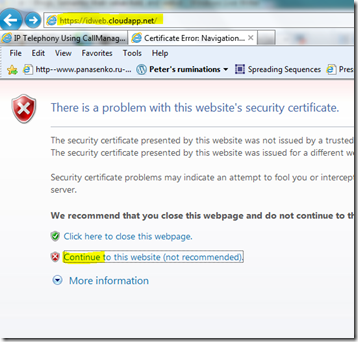
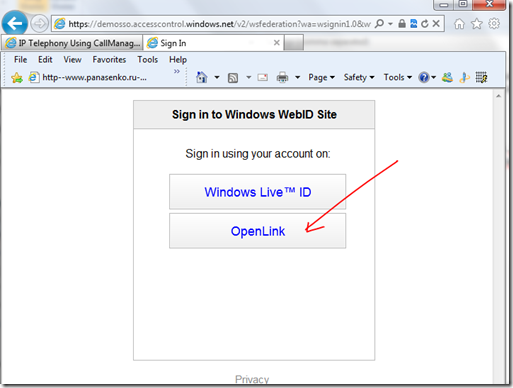
My target web site is https://idweb.cloudapp.net/. It challenges me to logon, using my choice of identity provider. I chose the option to use OpenLink – because it can now leverage my certificate AND my original profile, AND the fact that in my original profile I intended OpenLink to act as my identity provider (today) when doing a login to the likes of https://idweb.cloudapp.net/.
So let’s actually do it:
This relying party website is guarded by SSL – using keys that do not rely on browser makers or public CAs, however. Neither Mozilla (as browser maker and keeper of trusts) nor all the trusted CAs (e.g. Comodo) are exactly 100% trustworthy, given the facts. So, I make my own keying arrangements. Let’s continue, and we get…
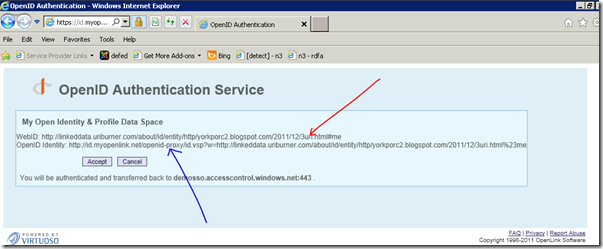
…whereupon we choose OpenLink.
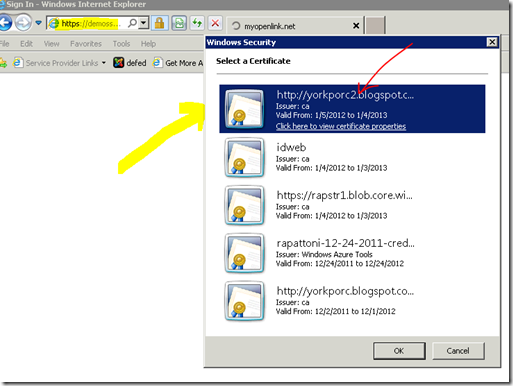
We get to choose our certificate, one of many shewn. And, do note the visible name. It’s our original blog site home page, even though we are about to assert our about-name — hidden deep within the technology.
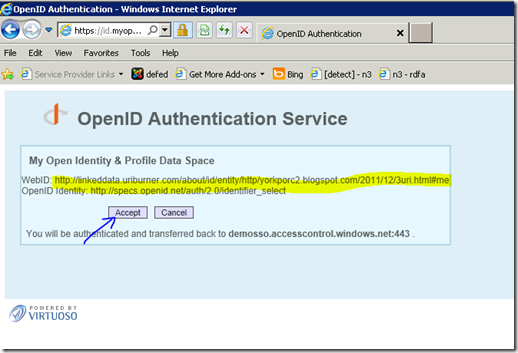
We get one last chance to opt out of the logon process (courtesy of some magic from Microsoft and OpenLink, based on the ws-fed and openid auth standards)…
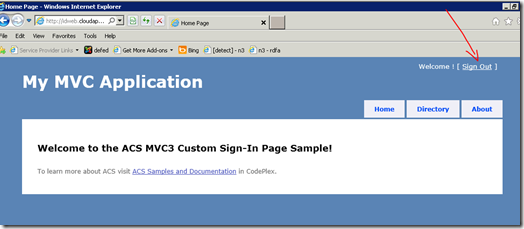
…and we land back on our desired site (with a session), ready to do a local logout:
Wow! The semantic web really works (and I have done NO programming). And it even works for logon via websso type processes, with the real world even.
Now let’s do it again, this time adding https security all the way through. We end up with the desired state…
…where now our handoff shows how the magic under the hood achieved all this!
Well done semantic web, and webid, and openid, and ws-federation (and SAML2 signed tokens).
As my boss (who paid for me to look at all of this) would say: “Its just magic”. And that’s how it’s supposed to be.
End.
`