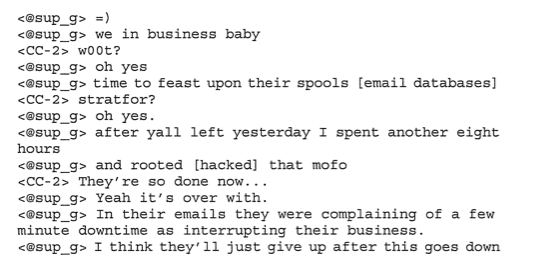
On December 6, 2011, a hacker using the handle "sup_g" private-messaged Hector Xavier Monsegur, otherwise known as "Sabu," on Anonymous's IRC server to tell him of a server he had gained access to. But "sup_g"—alleged by the government to be Jeremy Hammond—didn't know that the whole conversation was being logged by the FBI, and that Monsegur had turned confidential informant. "Yo, you round? working on this new target."
The target was the server of Stratfor, the Austin-based global intelligence company that would soon become synonymous with the hacker phrase, "pwned." Over the course of the Anonymous cell Antisec's hacking and exploiting of the company's IT infrastructure, the group of hackers would expose credit card and other personal information of over 60,000 Stratfor customers and a vast archive of e-mail correspondence between the company's employees and customers in the private and government sectors. And it all started with a control panel hack.
According to the FBI, Hammond, also more widely known by the handle "Anarchaos," sent Monsegur a link on a TOR network hidden server to a screenshot of Stratfor's administrative panel for its website. Antisec has used panel hacks to exploit a number of other sites, including the Federal Trade Commission's sites hosted on Media Temple.
Using SQL injection exploits against interfaces to the Web administration application, hackers have been able to gain low-level control over sites and do with them what they will. But in the process of exploiting the control panel, Hammond found there was potential for more than just a simple Web defacement in the Stratfor site. "This site is a paid membership where they gain access to articles," he messaged Monsegur . "It stores billing as well - cards. It's encrypted though. I think I can reverse it though but the encryption keys are store[d] on their server (which we can use mysql to read)."


 Loading comments...
Loading comments...
